- Digitalization
- Mobility & Infrastructures
Categories:
ISA/IEC 62443, formally known as ISA 99, is a series of international standards, specifications and technical reports were purpose-built to address security issues unique to Industrial Automation and Control Systems (IACS) and Operational Technology (OT). It has become the leading industrial cybersecurity standard for all types of plants, facilities and systems across industries, from manufacturing and processing plants to energy suppliers and rail.
Because the topic is so broad, a single document discussing all facets of risk analysis, design, operation, and maintenance was not practical. Instead, multiple documents were created that provide both normative requirements and supporting guidance on securing OT systems across a lifecycle and defining specific responsibilities and accountability for all roles, including asset owners, system integrators, suppliers, and service providers. But how can various roles share the responsibilities through ISA/IEC 62443 cybersecurity lifecycle? And how can you use the ISA/IEC 62443 based on your role?
ISA/IEC 62443 structure
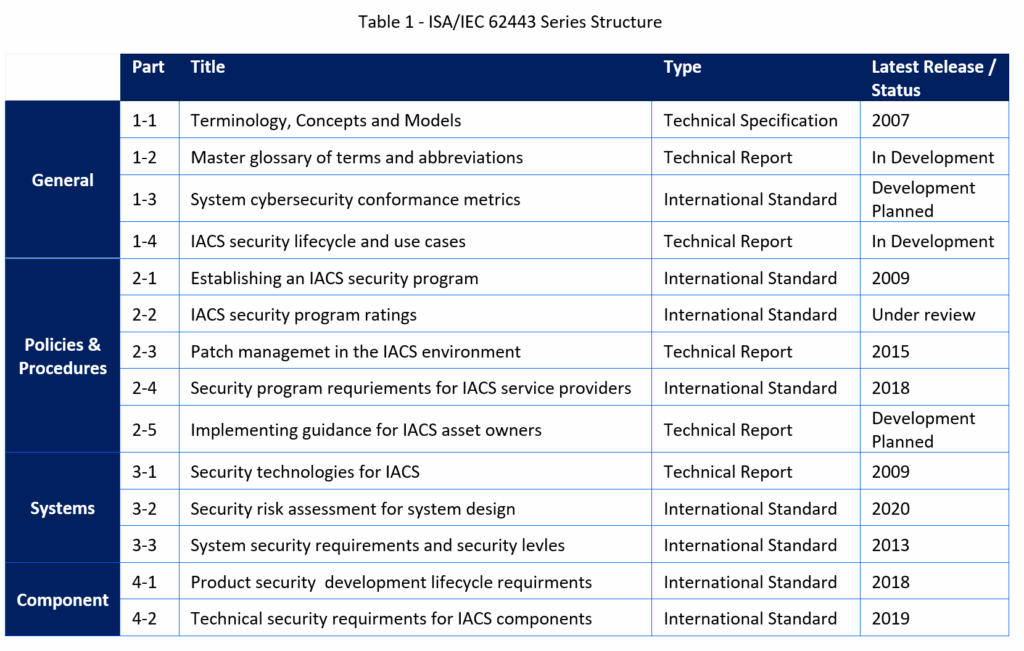
The ISA/IEC 62443 series of standards has made up 14 work products including Standards, Technical Specifications and Technical Reprots categorized into the following four tiers:
- Tier 1: General, provides an overview of the industrial security process and introduces essential concepts;
- Tier 2: Policies and Procedures, highlight the importance of policies – even the best security system is useless if people are not trained and committed to support it.
- Tier 3: Systems, provide essential guidance for designing and implementing secure systems.
- Tier 4: Components, describe the requirements that must be met for secured industrial components.
Some parts of ISA/IEC 62443 standrds are not published yet as ISA/IEC standards are on five years update cycle.
Table 1 shows the complete list of the current version of ISA/IEC 62443 standards and technical reports based on their types.
Prinicpal roles
The ISA/IEC 62443 standard targets a wide range of people, from suppliers to integrators and asset owners. To establish a robust and effective OT cybersecurity, all stakeholders share responsibility during all phases of the OT cybersecurity life cycle.
- Asset Owner is accountable for the cybersecurity risk of the IACS and responsible for the operation and maintenance of systems. Asset owner may engage Service provider with maintnenance capabaility that provides support activities for an Automation Solution.
- Product Suppliers are responsible for developing and distributing secure by design components, including Control Systems, Embedded Devices, Host Devices, Network Devices, and/or Software Applications.
- System Integrator is responsible for integration activities for an Automation Solution including design, installation, configuration, testing, commissioning, and handover to the Asset Owner.
Lifecycle view
Like many other standards about control systems for industrial applications, the ISA/IEC 62443 series employs a lifecycle approach to structure the tasks that must be accomplished, the inputs and outputs from those tasks, and the requirements that those tasks must achieve.
There are two independent lifecycles described in the series: The Automation Solution Security Lifecycle and the Product Security Lifecycle. The Automation Solution Security Lifecycle is further divided into an Integration Phase and an Operation and Maintenance Phase.
Table 2 shows the relationship between the Parts of the ISA/IEC 62443 Series and the various lifecycles and phases.
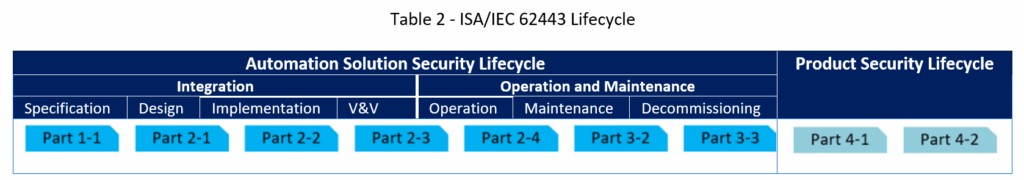
Automation solution security lifecycle
Automation Solution Security Lifecycle specifies the technical and administrative security measures in a particular facility and includes the following phases:
- Risk Assessment and Specification, includes identifying the System under Consideration (SuC), performing an initial high-level risk assessment, and partitioning the System into security zones and conduits. The result of this process is the Target Security Levels for each Zone and Conduit in the SuC.
- Design, determines the SuC and includes technical security measures (based on Security Levels) and Organisational security measures. Cybersecurity Requirement Specifictaion (CSRS) is the key deliverable from this phase that must be approved by Asset Owners before starting implementation.
- Implementation, is when the technical security measures specified in CSRS are implemented in IACS.
- Verification & Validation (V&V) , is when the IACS is tested to ensure that the technical and organizational security measures meet the security requirements specified in the CSRS. There are two main types of cybersecurity testing, Cybersecurity Factory Acceptance Test (CFAT) and Cybersecurity Site Acceptance Test (CSAT). Handovering the IACS to Asset Owner is the last step in V&V phase. Credentials should be changed before IACS is put into operation.
- Operation, is when the IACS is placed into service and all of the organizational and technical security measures are executed. Technical and organizational security measures and associated IACS risk assessment must be periodically reviewed and updated.
- Maintenance, is triggered by Operations requests or the monitoring of security threats and security vulnerabilities. Changes to address security threats or vulnerabilities must be implemented through Management of Change process that includes risk assessment.
- Decommissioning, can be triggered by a maintenance activity or by major upgrade or at the end of the project. In either case, the decommissioning must be done in such a way that the Asset Owner’s on-going operations are not compromised. IACS sensitive data must be destructed or purged at this phase.
The security program must be established and maintain throughout the entire Automation Solution Security Lifecycle.
Product security lifecycle
The Product Security Lifecycle specifies the security requirements used to design, develop, and support IACS products including secure by design aspects and secure implementation. The integration of comprehensive security controls such as design review, threat modeling, security verification & validation testing, and security update management into the product lifecycle ensures that the risks are identified and an appropriate mitigation is provided prior to the product release.
Part 4-1 describes process security requirements (e.g., policies and procedures) for the Security Lifecycle of IACS System and Component product development and support. Part 4-2 specifies the technical security requirements for IACS components based on Security Levels that allow the Product Supplier to deliver and support a product. The prinicpal audience of these two parts are Product Suppliers of IACS system and component products.
The product security lifecycle is orgonised around eight practices as listed below:
- Security management, intended to ensure that security related activities are adequately planned, documented and executed through the product’s lifecycle.
- Specification of security requirements, intended to define and document the security capabilities of the product and the expected product security context.
- Secure by design, intended to ensure that the appropriate security considerations have been included throughout the specification and design phases of product development, based on the defense in depth strategy.
- Secure implementation , intended to ensure that product functionality and security measures are implemented securely.
- Security verification and validation testing, intended to ensure that the security requirements have been met for the product, and security of the product is maintained when it is used in its security context and configured according to the defense in depth strategy.
- Managmengt of security related issues, are used for handling security-related issues of a product that has been configured to employ its defense in depth strategy within the product security context.
- Security update management, intended to ensure security updates associated with the products are tested for regressions and made available to product users in a timely manner.
- Security guidelines, intended to provide user documentation that describes how to integrate, configure, and maintain the defense in depth strategy of the product in accordance with its product security context.
The ISA/IEC 62443 standards are the most comprehensive and exhaustive cybersecurity standards available to the critical infrastructure domains and industrial sectors, which describe cybersecurity reference architectures, direction for security lifecycles, processes, requirements, technology, controls, testing, product development and a cybersecurity management system. These standards provide a set of common terms and requirements that can be used by Asset Owners, Product Suppliers and Service Providers to secure their industrial automation and control systems and the equipment they control.
To understand how to use the ISA/IEC 62443 Series it is first necessary to understand the relationship between roles that are identified in these standards. Therfore development of a cybersecurity framweork and Term of Refernce (TOR) early in the proejct is one of the most important project success factors.
- cybersecurity
Tags:
Soroush Tazerji
Director de servicios de seguridad de Tactix Sener Group
Soroush is Director of Security Services at Tactix Sener Group. He has extensive experience in large-scale railway projects in Australia, North America, and the Middle East. His expertise encompasses full project lifecycle management, including the design, implementation, testing, installation, commissioning, and operation of cybersecurity technology systems and operations. He has successfully provided cybersecurity solutions for various ICS/IACS systems, managed major cybersecurity improvement programs, and established cybersecurity operations and response units that are part of the Cybersecurity Operations Center (CSOC) for Critical Infrastructure. He also contributed to the development of international cybersecurity standards and automation and control systems.