- Digitalization
- Mobility & Infrastructures
Categories:
Delivering excellent safety performance is a given for any critical infrastructure project. Avoiding incidents, and damage to human health, nature and equipment is a key reason for safe design and operation.
Historically, Operational Technology (OT) systems like SCADA, DCS, PLC and Signaling were isolated and ran on proprietary hardware, programs and protocols. Demands for less expensive and easier to use OT products brought the use of open technologies to OT, and digital transformation brought more connectivity.
In today’s industrial environment cyber-threats are very real as demonstrated by high profile attacks in recent years. A cyberattack on OT can compromise the integrity or availability of these systems and disrupt or damage physical assets, disrupt operations, injure people, or cause severe environmental damage to the surrounding area. Cybersecurity is important because it protects your OT systems from potential cyber threats, and you cannot have a safe system if it does not have the appropriate cybersecurity properties. But what is the best way to assure both safety and security of OT systems?
Why is OT Cybersecurity important?
The critical infrastructure sector has been focused on safety for years. The extensive use of communication and the shift to smart and more connected technologies, introduces security concerns for Operational Technologies (OT) used in this sector, where typically security has not been an issue before. Cyber-attacks are growing in significance and the consequences can be catastrophic, especially when perpetrated by state sponsored threat actors. State sponsored actors are usually highly motivated, with sophisticated skills and unlimited resources at their disposal. Poor cybersecurity posture can result in vulnerabilities that can leave a facility open to attacks that could result in financial harm, equipment damage, disruption of service and even loss of life. This means that there is a need to refocus attention on both Functional Safety and Cybersecurity, while ensuring that neither compromises the other. It is possible to apply safety and cybersecurity to an OT system separately, but the real issue concerns the interaction between the two.
Many conversations regarding OT cybersecurity often circle back to safety because it is one of the cornerstones of operations. OT Cybersecurity, like safety, approaches issues based on managing risk, leveraging continuous assessment, and baselining to ensure risk is managed to a tolerable level.
What do core standards say?
Today, both cybersecurity and functional safety standards are recognizing these risks:
Cybersecurity standard ISA/IEC 62443-1-1, Section 4.1:
“… However, because industrial automation and control systems equipment connect directly to a process, loss of trade secrets and interruption in the flow of information are not the only direct consequences of a security breach. The potential loss of life or production, environmental damage, regulatory violation, and compromise to operational safety are far more serious consequences. These may have ramifications beyond the targeted organization; they may grievously damage the infrastructure of the host region or nation.”
Functional safety standard IEC 61508 -1 7.4.2.3:
“The hazards, hazardous events and hazardous situations of the EUC and the EUC control system shall be determined under all reasonably foreseeable circumstances (including fault conditions, reasonably foreseeable misuse and malevolent or unauthorized action). This shall include all relevant human factor issues, and shall give particular attention to abnormal or infrequent modes of operation of the EUC. If the hazard analysis identifies that malevolent or unauthorized action, constituting a security threat, as being reasonably foreseeable, then a security threats analysis should be carried out.”
There are significant overlaps between these types of processes, that are followed to minimize dangerous failures and minimize security vulnerabilities as shown by the high-level overview in Fig.1.
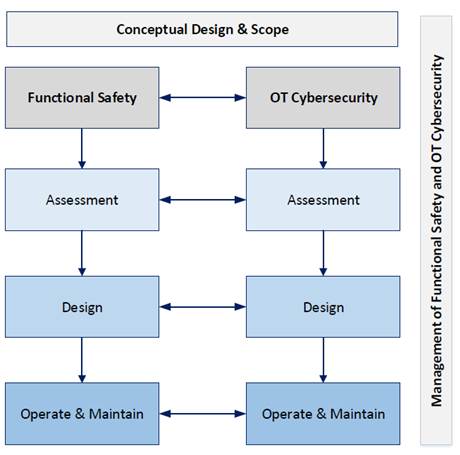
Figure 1Management of Functional Safety and Cybersecurity
What is an Integrated Lifecycle?
As both functional safety and OT cybersecurity standards require the mitigation of risks to a tolerable level, it is recommended that the cybersecurity development lifecycle be closely intertwined with the functional safety development lifecycle. This will reduce the impact of the security requirements by leveraging the commonalities with the safety development lifecycle, and early identification of trade offs in safety and cybersecurity requirements.
In many industrial environments, project owners are starting to place security in the same importance as safety. Safety systems, if compromised with a cyberattack, could be prevented from performing their safety functions correctly, potentially leading to a hazardous situation. Therefore, cybersecurity concerns should also be addressed in addition to safety when considering risk mitigation strategies.
This shift in mindset requires a new culture that transforms the current approach of OT cybersecurity and functional safety as two entirely separate disciplines into one, where cybersecurity and safety concerns are integrated into one uniform approach to risk. The earlier the integration of cybersecurity and safety, the greater the benefits that can be reaped.
For effective integration, the vulnerability to a cyber-attack needs to be considered during each phase of the functional safety lifecycle. Ideally, safety hazard and cyber-threat identification would coincide so that engineers can consider solutions that eliminate or reduce the risks from both sources. The outcome would be an integrated set of functional requirements that embrace both safety and cybersecurity requirements, and ultimately a compliant design and effective supporting management system.
To efficiently manage both safety and security requirements and promote workflow, comprehensive functional safety and cybersecurity lifecycles have been developed. Fig.2 shows a high-level guideline, and it should be tailored as every facility is unique and requires a specific lifecycle to manage both safety and security risks.
Rigorously following these lifecycles facilitates efficient engineering and allows for completing all required tasks for the cybersecurity and safety lifecycles. Furthermore, an integrated lifecycle approach aligns team members with the key requirements for both safety and security activities.
As discussed briefly, functional safety of systems can be compromised by cyber threats, and in this respect, Cybersecurity is of the same importance as safety and should be treated as a must-have for any OT system. Integrated Cybersecurity & Functional Safety (ICSFS) management is an investment resulting in profit on the bottom line – even if it is not always that obvious.
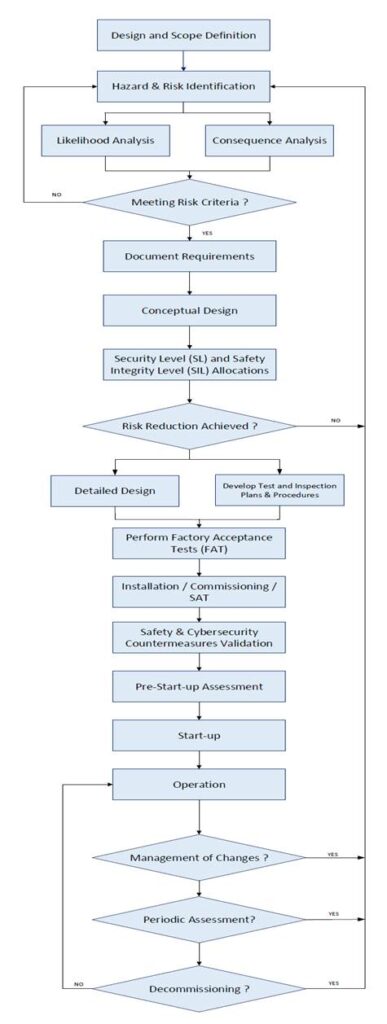
Figure 2 High-Level Guideline to ICFS Lifecycle
- cybersecurity
Tags:
Soroush Tazerji
Director de servicios de seguridad de Tactix Sener Group
Soroush is Director of Security Services at Tactix Sener Group. He has extensive experience in large-scale railway projects in Australia, North America, and the Middle East. His expertise encompasses full project lifecycle management, including the design, implementation, testing, installation, commissioning, and operation of cybersecurity technology systems and operations. He has successfully provided cybersecurity solutions for various ICS/IACS systems, managed major cybersecurity improvement programs, and established cybersecurity operations and response units that are part of the Cybersecurity Operations Center (CSOC) for Critical Infrastructure. He also contributed to the development of international cybersecurity standards and automation and control systems.